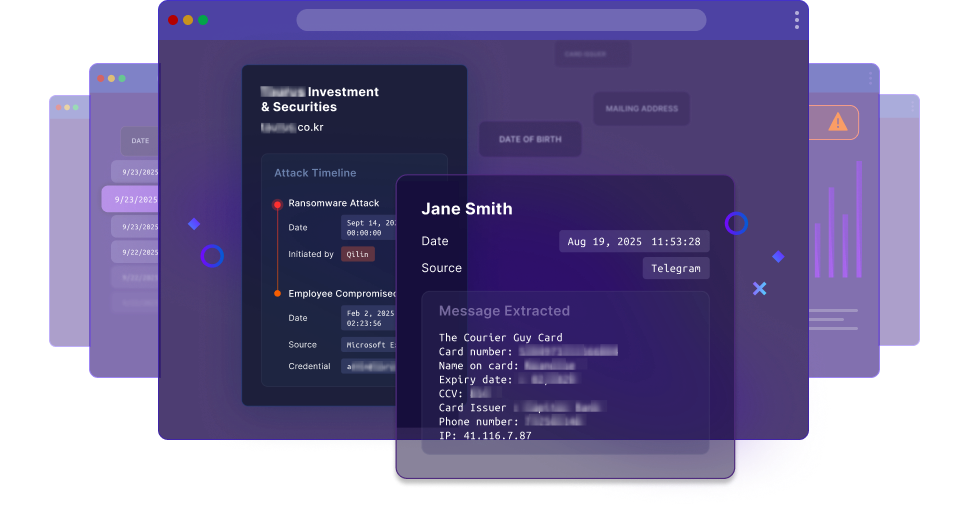
We’ve identified compromised breaches months before ransomware attacks
Fresh datapoints added every single day
Platform uptime that provides security and confidence
To get “armored” up— no installation or messy overhead necessary

Data is collected autonomously from active and ongoing attacks in addition to threat intel and dark web monitoring

Data is aggregated, cleaned, and analyzed to identify asset ownership so that you get the full picture without the additional noise.

You get actionable alerts about compromises like PII, hijacked MFA sessions, stolen credit card details, emails and passwords.







The average cost of a data breach in the USA in 2025, more than 2x the global average (IBM)
Average savings when a breach is detected internally vs disclosed by an attacker (IBM)
Increase of credential theft due to AI powered phishing and malware-as-a-service (ITPro)
Reduction in incident response time for MSSPs that use dark web monitoring (webz)

Detect and respond to threats faster with advanced forensics relevant to your organization

Enhanced hunt data not available elsewhere

Incident attribution & actor profile

Ensure compliance and improve audit readiness

Reduce response time

Easy API integration

Enhance your services with dark web monitoring and identity asset remediation.

Detect infostealer, malware, unauthorized purchases, exposed PII and more

Minimize risk exposure

Multi-tenant architecture

Easy API integration

Scalable pricing based on your needs

We offer a lightweight solution so you can get visibility on your digital footprint and stay one step ahead of cybercriminals.






Get proactive, prebreach intelligence

Be an early adopter with enhanced support and input on feature development

Limited time early adopter pricing

Get an edge over your competition

DarkArmor collected and analyzed over 3000 screenshots from a Nigerian cybercriminal’s desktop, and what we uncovered goes far beyond the outdated image of “419 scams”. Learn how automation helped him launch attacks at scale.
Download